Protect Your Passwords|
Data breaches are on the rise, and cybercriminals are becoming more inventive with their ways of infiltrating companies to extract sensitive information. With over 80% of data breaches being associated with weak, shared and reused passwords, it highlights the importance of improving password security to protect organisations.
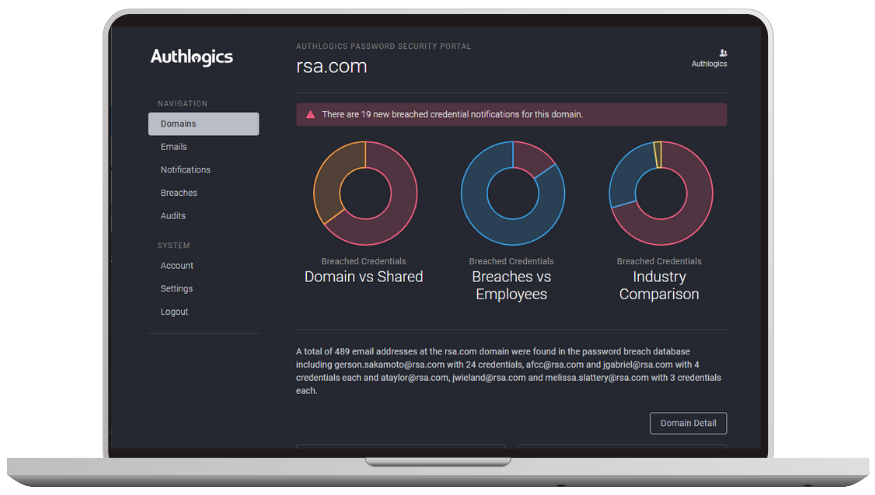
The Authlogics Password Breach Database receives over one million updates daily. It is the largest enterprise compilation with over 6 billion compromised clear text credentials, making it 55% larger than common free database.
Understand your threat profile on the dark web.