Real-Time
Password Protection|
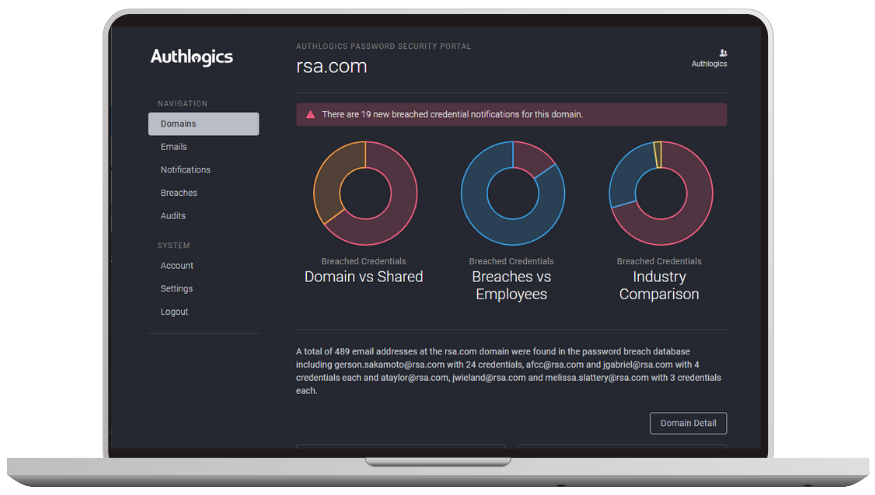
No matter your cyber security processes and practices, with just ONE weak password… YOU ARE AT RISK!
Want to identify the individuals utilising poor password practices and provide them with password feedback guidance?
Benefit from real-time password protection by accessing the largest enterprise-grade Password Breach Database which holds over 6 billion compromised credentials.