Password Security & Compliance
Automated Real-Time Protection
Simplified Authentication
Ultimate User Login Experience
Day-One Deviceless Access
Rapid Deployment, Ease of Integration
Identity Verification
Customer Cost & Risk Reduction
Login Adaptability
Cloud & On-Prem Hybrid Versatility
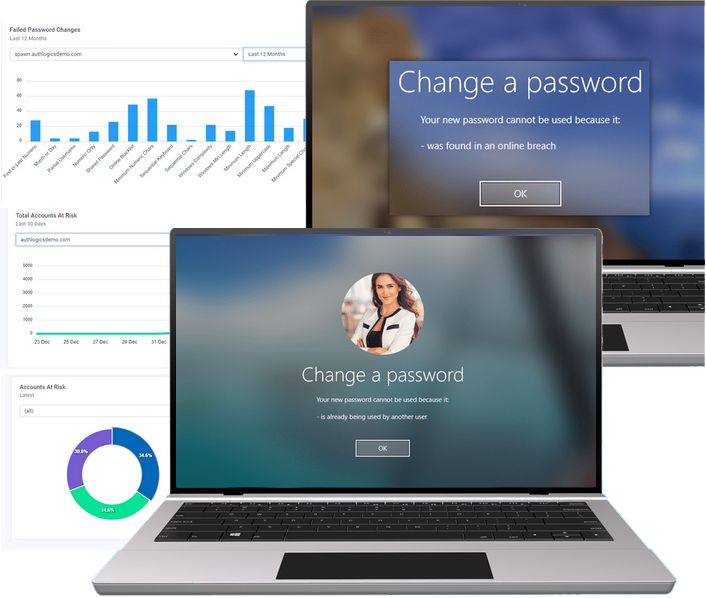
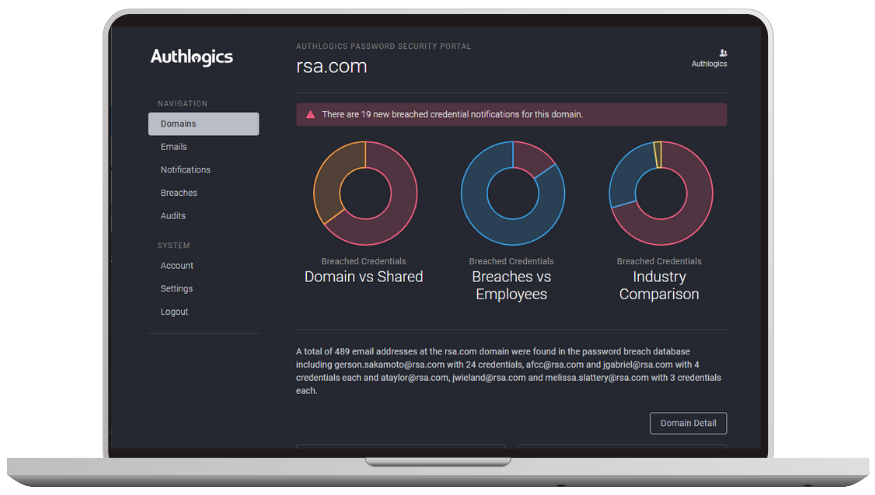
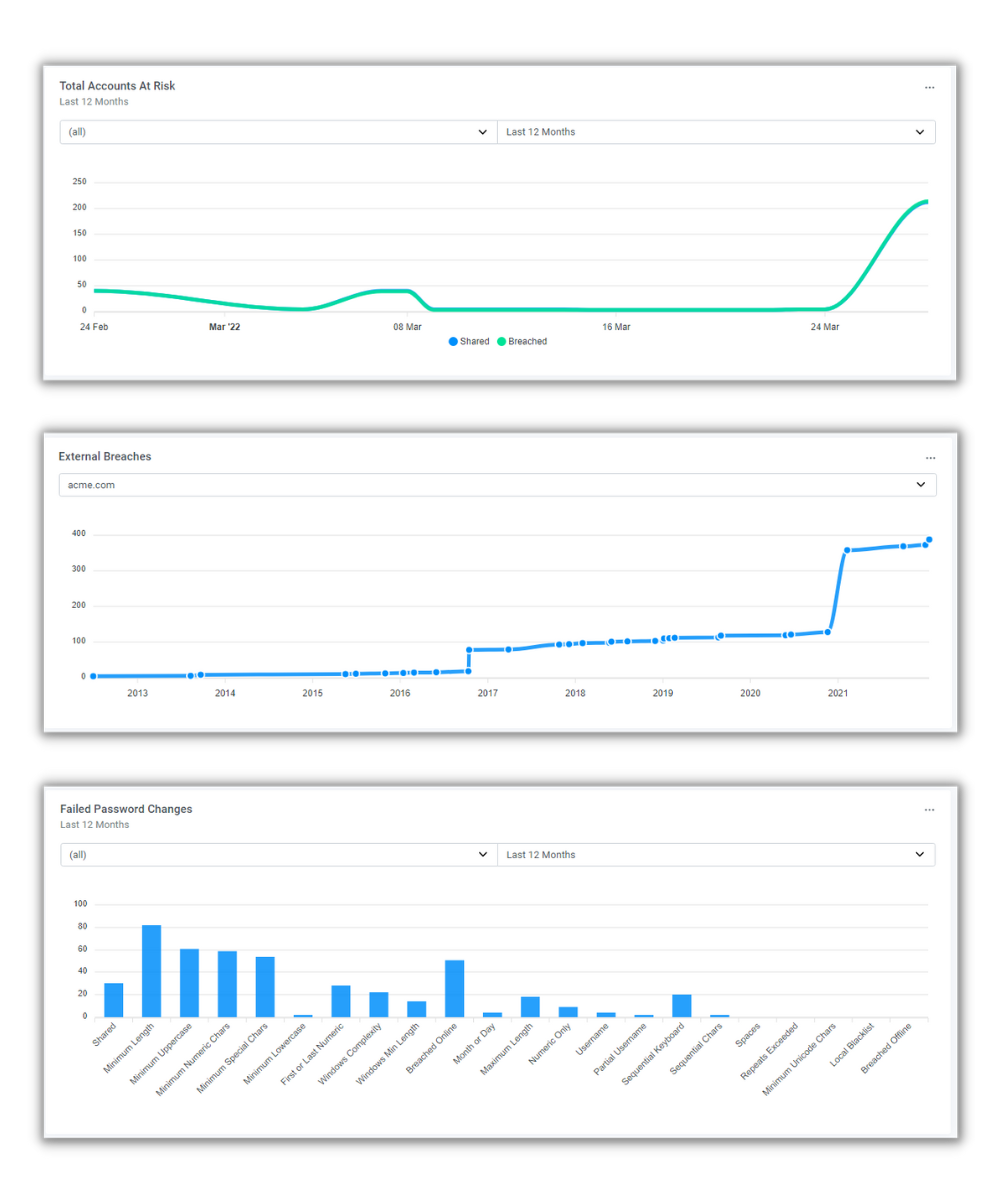
Password Breach Database
Identify poor password practices
Password Security Audit
Assess your Active Directory
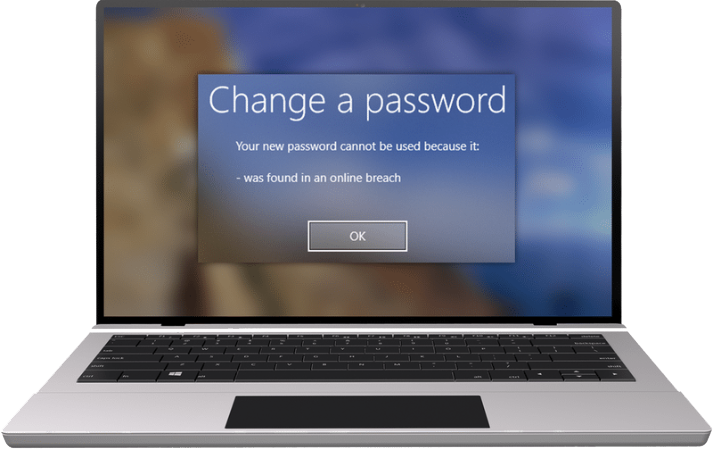
Password Security Management
Real-time protection and remediation
Demo Videos
See Authlogics in action
Resources
Datasheets, case studies and whitepapers
Blog
News and information updates
Cost Saving
Calculate the benefits