Complimentary Gartner® Report
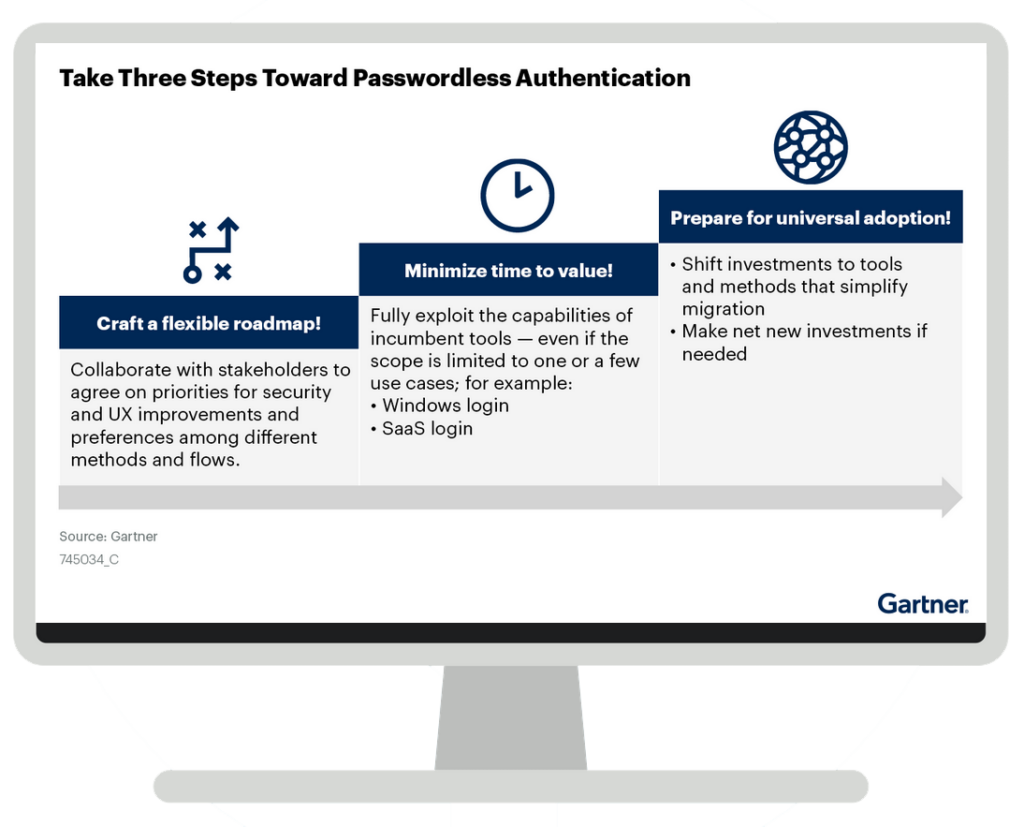
Take 3 Steps Toward Passwordless Authentication
“Eliminating login passwords can improve both UX and security, but passwordless authentication is not a discrete technology or a distinct market. SRM leaders responsible for IAM must carefully identify their objectives and options to prioritize time to value along the path to a passwordless future.”
ID G00745034


